Passwords have long been a major security concern, with the majority of security incidents arising from stolen or weak passwords. In our post about password health, we discussed methods to reduce the risk of accounts being compromised. In this article, we’ll review conditional access, which is an additional layer of protection that your organisation can implement.
What is conditional access
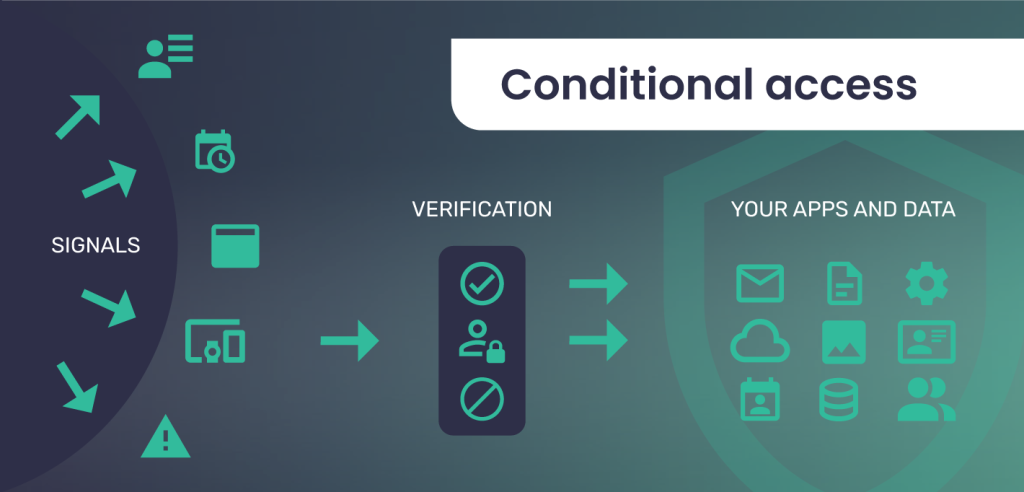
Conditional access is a method of controlling access to data or services for your organisation’s users and accounts. Conditional access policies are implemented to ensure checks are carried out before access is granted. For example, if a user attempts to access a specific resource, a conditional access policy could require that multi-factor authentication is applied.
Signals used for conditional access
A variety of factors (known as “signals”) can be used when implementing conditional access policies. Some of the most common signals are shown below:
- IP and geographic location
- The device being used
- The application being used
- The time of day access is requested
- The type of user
- Risky sign-in behaviour
Commonly applied policies
A variety of policies can be required before access is granted. Some of these are based on the signals listed above:
- Allow trusted locations
- Require multi-factor authentication
- Block locations or regions
- Block risky sign-in behaviours
- Require organisation-owned devices for specific applications
How conditional access can improve the login process for your team
Not all users must use MFA when they are in a trusted location, using a trusted device. This means you can reduce the need to use MFA for users that are logging-in from your office when using an organisation-owned device. This helps speed up the login experience for many users.
Additional layers of security
You can tailor extra challenge questions on a role or context-specific basis, ensuring that only specific users with special access are subjected to additional verification measures.
You could also restrict access to data based on a staff member’s role and can also use conditions in combination, such as lowering permissions to view-only if a user is logging in with an unknown device or from an unknown location.
Reduce risk with the principle of least privilege
The rule of least privilege is the practice of only granting the lowest level of access and permissions that are necessary for a user to do their work. We recommend adopting a proactive approach to access management by conducting regular access reviews and continuously monitoring user activity, as this will help to identify and reduce any access-related risks.
How we can help
We carry out user audits and implement conditional access policies for our managed IT customers. You can contact us today to find out how we can help with your cyber security needs.
